Detecting eDellroot Certificate using K1000
I already have a script that runs the removal tool for the eDellroot certificate, but I was wondering if anyone has a way to detect the certificate. At the very least, a way to do it in the verify part of the removal script, so I can avoid running it on machines that do not have the cert. Ideally, I'd like to be able to do a custom inventory rule to actively monitor how many devices have the cert installed.
0 Comments
[ + ] Show comments
Answers (4)
Answer Summary:
Please log in to answer
Posted by:
ashlea
9 years ago
Top Answer
These two powershell commands will also give the output "Found Certificate" if the problem certs are found. Could output this with the hostname to a file to get a list of affected machines.
Get-ChildItem -Path cert:\LocalMachine\Root | Where-Object {$_.Subject -like "*eDellRoot*"} | ForEach-Object {Write-Host "Found Certificate"}
Get-ChildItem -Path cert:\LocalMachine\Root | Where-Object {$_.Subject -like "*DSDTestProvider*"} | ForEach-Object {Write-Host "Found Certificate"}
Comments:
-
I must've missed your answer here so I deleted my comment below! My solution was the same except the last pipe was to Out-File so I could import the text file as a CIR and generate a report. - getElementById 9 years ago
Posted by:
rileyz
9 years ago
http://www.itninja.com/question/edellroot-certificate-uninstall-using-k1000
In my post there is a bit of code you can adapt for your needs, or it might help atleast. You will need to use certutil.exe, unless your machines have the cmdlets to mess around with certs.
I would try and detect/query it via serial number if it allows, failing that get the output of the cert store to a variable, then search the varible for the cert serial number.
My use case was drivers and Windows 7, hence certutil.
Posted by:
ashlea
9 years ago
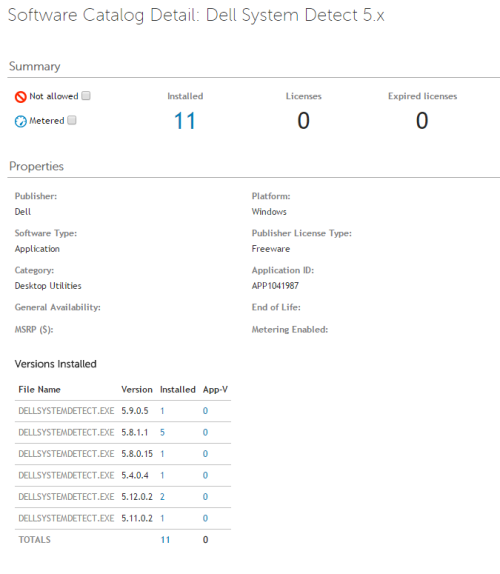
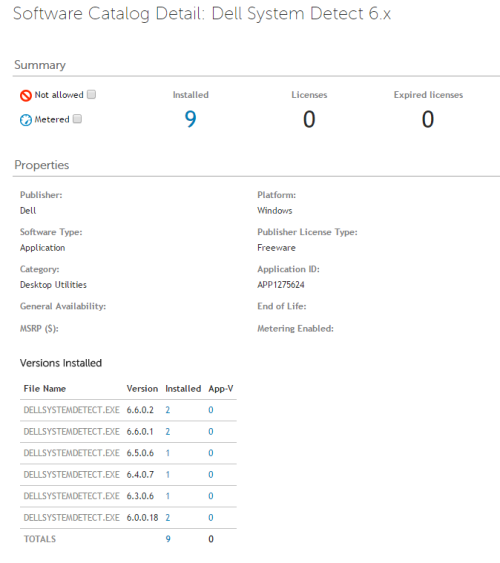
I ended up using a combination of discovered software, processes, and startup programs detected by Kace to look for the Dell System Detect Software. Fortunately, of the 25 machines that had the probability of having that software (out of 991 total devices), so far we have not found one that has. I targeted those 25 machines for the removal script and told users to expect a pop-up. We spot-checked 5 of the computers before pushing the script and they didn't have the cert anyway, so we're just doing it as a precaution. This was the quickest remediation plan I was able to come up with.




Posted by:
jknox
9 years ago
https://dellupdater.dell.com/Downloads/APP009/eDellRootCertificateRemovalInstructions.pdf
Edited to add: there is apparently a new removal tool according to this article: https://dellupdater.dell.com/Downloads/APP009/DellCertFix.exe
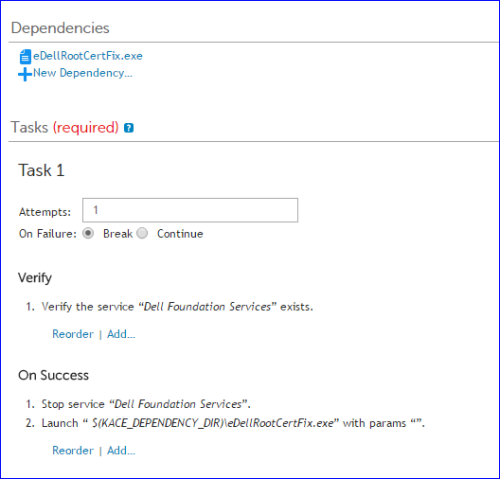
Edited to add: there is apparently a new removal tool according to this article: https://dellupdater.dell.com/Downloads/APP009/DellCertFix.exe
I think I'd just use an online kscript. I don't have the cert to test with, but I think this should work using the executable from the above link:

Comments:
-
As my original post states, I already have a script that removes the certificate. I am using Dell's removal tool in a kscript. I'm talking about detecting whether their cert is installed via a custom inventory rule. I want to be able to say with 100% certainty that the cert is not on any of our devices. If I had the bad cert, I could import it into untrusted certificates in our group policy and call it good... But I don't.
Verifying "Dell Foundation Services" didn't seem like a good option as the removal instructions seem to indicate that it's needed for other software, considering they only have you stop and then restart the service, rather than removing it. - ashlea 9 years ago



